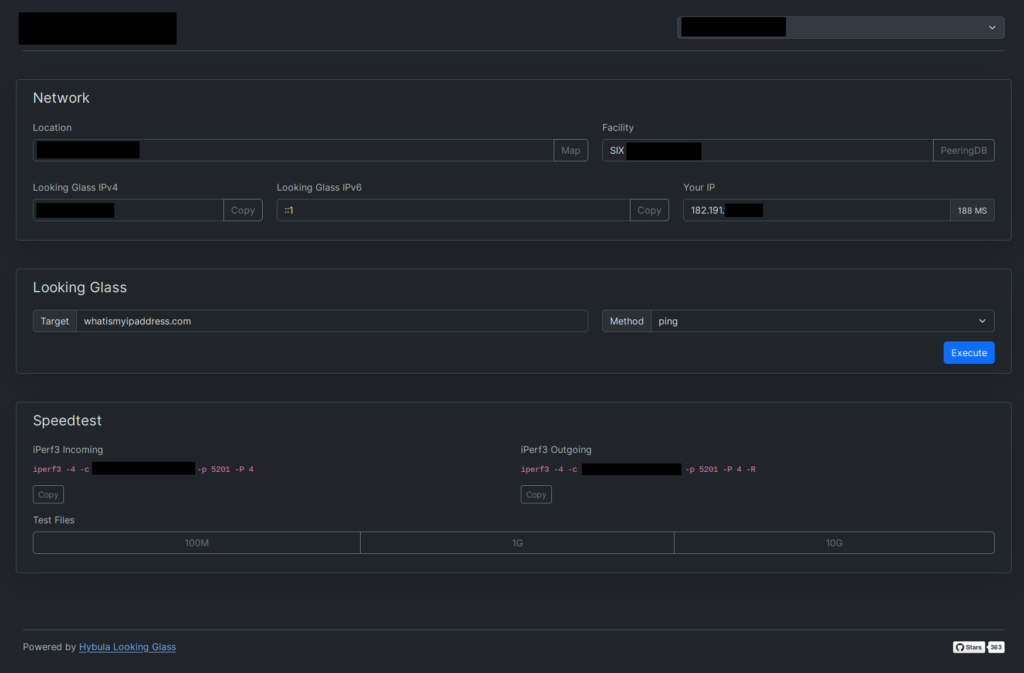
Looking Glass is a powerful network-related utility written in PHP and Bootstrap 5. It can run network commands directly in the browser. The setup is pretty straightforward if you follow the documentation. However, in this guide, we will install it manually using Apache as the web server and obtain an SSL certificate from Let’s Encrypt. So, read on to learn how to install Looking Glass on AlmaLinux 9.
Without further ado, let’s get started.
Install the required tools
We will install all the required tools and libraries needed for this setup, including PHP and Apache.
dnf install mtr traceroute httpd mod_ssl php-fpm php-posixStart and enable PHP-FPM and Apache at boot time.
systemctl start httpd
systemctl start php-fpm
systemctl enable httpd
systemctl enable php-fpmAdd firewall rules for HTTP and HTTPS:
firewall-cmd --permanent --zone=public --add-service=http
firewall-cmd --permanent --zone=public --add-service=https
firewall-cmd --reloadAs suggested disable SELINUX.
vim /etc/selinux/configAnd set SELINUX=disabled.
Create symlinks for MTR and it’s helpers:
ln -s /usr/sbin/mtr /usr/bin/mtr
ln -s /usr/sbin/mtr-packet /usr/bin/mtr-packetDownload Looking Glass
We will now download the latest version of Looking Glass as an archive and unzip it.
cd /var/www/
wget https://github.com/hybula/lookingglass/archive/refs/heads/main.zip
unzip main.zip
mv lookingglass-main/* /var/www/htmlIt is advisable to create some dummy files for download and set up the configuration according to our needs.
mv /var/www/html/config.dist.php /var/www/html/config.php
mkdir /var/www/html/files
truncate -s 100M /var/www/html/files/dummy-100M.bin
truncate -s 1G /var/www/html/files/dummy-1G.bin
truncate -s 10G /var/www/html/files/dummy-10G.bin
chown -R apache:apache /var/www/htmliperf3 (optional)
This is not required, but if you want to install it, here you go.
dnf install iperf3 -y
iperf3 -sD -p 5201To automatically start iperf3 when the system boots up, create a systemd unit file.
vim /etc/systemd/system/iperf3.serviceAdd the following in it:
[Unit]
Description=iperf3 server
After=syslog.target network.target auditd.service
[Service]
ExecStart=/usr/bin/iperf3 -s
[Install]
WantedBy=multi-user.targetStart and enable it:
systemctl start iperf3
systemctl enable iperf3SSL and Apache virtual host
Add the EPEL repository to the system for the Certbot package.
dnf install epel-release
dnf install certbotCreate a virtual host file based on your domain.
vim /etc/httpd/conf.d/DOMAIN.COM.confAdd the following in it:
<VirtualHost *:80>
ServerName DOMAIN.COM
ServerAlias DOMAIN.COM
DocumentRoot /var/www/html
ErrorLog /var/log/httpd/DOMAIN.COM_error.log
CustomLog /var/log/httpd/DOMAIN.COM_access.log combined
</VirtualHost>Check the configuration and restart Apache.
apachectl configtest
systemctl restart httpdOnce the host is set up, it’s time to get an SSL certificate from Let’s Encrypt.
certbot certonly --webroot -w /var/www/html -d DOMAIN.COMNote down the paths to the certificate files and open the virtual host file to add the port 443 block.
<VirtualHost *:443>
ServerName DOMAIN.COM
DocumentRoot /var/www/html
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options "SAMEORIGIN"
Header always set X-Content-Type-Options "nosniff"
Header always set X-XSS-Protection "0"
Header always set X-Permitted-Cross-Domain-Policies "none"
Header always set Referrer-Policy "no-referrer-when-downgrade"
Header always set Permissions-Policy "camera=(self), geolocation=(self), microphone=(self)"
Protocols h2 http/1.1
<Directory "/var/www/html">
AllowOverride All
Options -Indexes +FollowSymLinks
</Directory>
ErrorLog /var/log/httpd/DOMAIN.COM_ssl_error.log
SSLEngine on
SSLCertificateKeyFile /etc/letsencrypt/live/DOMAIN.COM/privkey.pem
SSLCertificateFile /etc/letsencrypt/live/DOMAIN.COM/fullchain.pem
</VirtualHost>apachectl configtest
systemctl restart httpdYou can test the URL with HTTPS. If it works, we can now add redirection from HTTP to HTTPS in the port 80 block.
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}apachectl configtest
systemctl restart httpdTo auto-renew the SSL certificate, add a crontab entry by running crontab -e.
30 04 * * * certbot renewAt this point, reboot the server to test all configurations and settings, such as the iperf3 daemon.
The main configuration file is located at /var/www/html/config.php.