Snipe-IT is an asset management system which can be self hosted too. It provides user friendly UI and has a powerful API. In this guide I will show you how to install Snipe-IT on Ubuntu 22.04 LTS with PHP 8.1 and MariaDB.
Before we start let’s list the basic requirements.
- PHP 7.4 and above
- MySQL or MariaDB
- PHP Imagick and GD libraries
Snipe-IT provides three methods for installation, we will use the source code method.
1- Install PHP, Apache and MariaDB
Update and upgrade your system first.
apt update && apt upgradeInstall PHP, Apache, MariaDB and the required PHP extensions, libraries.
apt install apache2 mariadb-server libapache2-mod-php8.1 php8.1 php8.1-gmp php8.1-bcmath php8.1-gd php-json php8.1-mysql php8.1-curl php8.1-mbstring php8.1-intl php8.1-imagick php8.1-xml php8.1-zip php8.1-fpm php8.1-redis php8.1-apcu php8.1-opcache php8.1-memcache php8.1-memcached php8.1-ldap bzip2 zip unzip imagemagick vimEnable Apache modules.
a2enmod ssl rewrite headers proxy proxy_http deflate cache proxy_wstunnel http2 proxy_fcgi env expiresWe will use PHP FPM. For that we will disable prefork module and enable event module.
a2enconf php8.1-fpm
a2dismod php8.1
a2dismod mpm_prefork
a2enmod mpm_event
systemctl restart apache2
systemctl enable apache2
systemctl enable mariadb
systemctl enable php8.1-fpmIf you would like to configure some options in php.ini, it is available in /etc/php/8.1/fpm/php.ini.
Some of the basic options to change are:
- max_execution_time = 180
- memory_limit = 512M
- post_max_size = 200M
- upload_max_filesize = 200M
- date.timezone = Europe/London
Save and restart PHP FPM.
systemctl restart php8.1-fpm2- Database setup
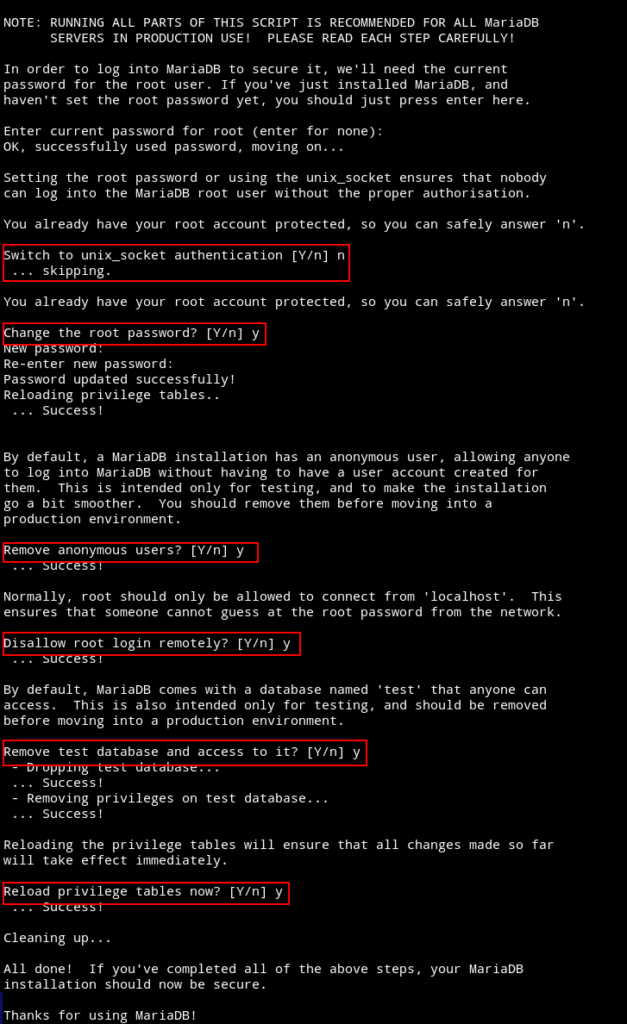
Run /usr/bin/mysql_secure_installation to configure the database.
Login to the database server and create a database.
mysql -u root -p
create database snipeit CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci;
grant all on snipeit.* to 'snipeit_user'@'localhost' identified by 'PASSWORD';
flush privileges;
exit3- Apache vhost
Create a virtual host file in /etc/apache2/sites-available/. I will name it as snipeit.conf.
vim snipeit.confInclude the following in it.
<VirtualHost *:80>
ServerName DOMAIN.COM
ServerAlias DOMAIN.COM
DocumentRoot /var/www/html
<Directory "/var/www/html">
Allow From All
AllowOverride All
Options -Indexes +FollowSymLinks
</Directory>
ErrorLog /var/log/apache2/DOMAIN.COM-error.log
</VirtualHost>Enable the virtual host and restart Apache.
a2dissite 000-default.conf
a2ensite snipeit.conf
apachectl -t
systemctl restart apache24- SSL certificate from LE
To get a free SSL certificate from Let’s Encrypt, install the snap package for it.
snap install certbot --classicNow if you have already pointed your domain to the server IP, get a certificate.
certbot certonly --webroot -w /var/www/html -d DOAMIN.COM5- Apache vhost 443 block
If you already have SSL certificates at hand, your 443 Apache vhost block would like the following.
You can do this later also once the propagation is completed.
<VirtualHost *:443>
ServerName DOMAIN.COM
DocumentRoot /var/www/html
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4
SSLProtocol All -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
Protocols h2 http/1.1
<Directory "/var/www/html">
Allow From All
AllowOverride All
Options -Indexes +FollowSymLinks
</Directory>
ErrorLog /var/log/apache2/DOMAIN.COM-error.log
SSLEngine on
SSLCertificateKeyFile /etc/letsencrypt/live/DOMAIN.COM/privkey.pem
SSLCertificateFile /etc/letsencrypt/live/DOMAIN.COM/fullchain.pem
</VirtualHost>Check and restart Apache.
apachectl -t
systemctl restart apache26- Download and install Snipe-IT
We are done with our server setup and it’s time to download install Snipe-IT app.
The latest version at the time of writing this article is 6.0.14. Let’s download that.
cd /var/www
wget https://github.com/snipe/snipe-it/archive/refs/tags/v6.0.14.zipUnzip and move it to html directory.
unzip v6.0.14.zip
rm -r /var/www/html/*
shopt -s dotglob
mv v6.0.14/* html/Change directory ownership.
chown -R www-data:www-data /var/www/htmlClean up:
rm -r v6.0.14
rm v6.0.14.zipIf everything is in place, navigate to your browser and begin the installation process.
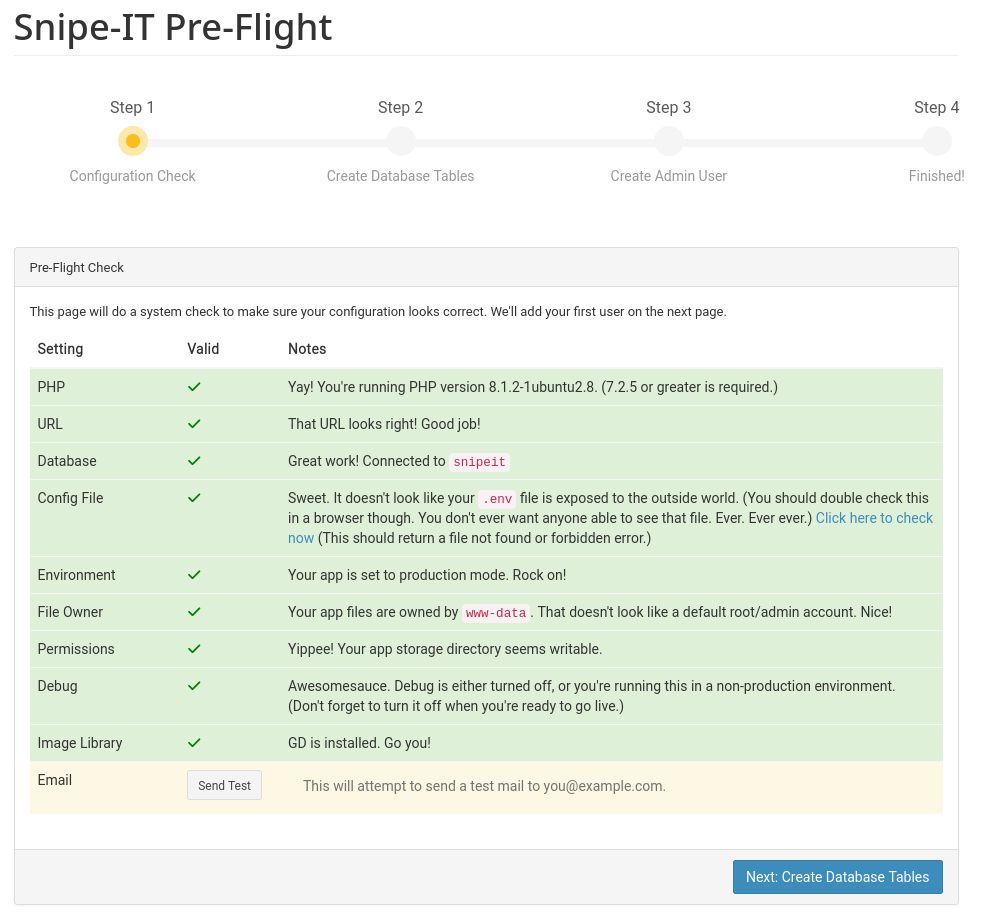
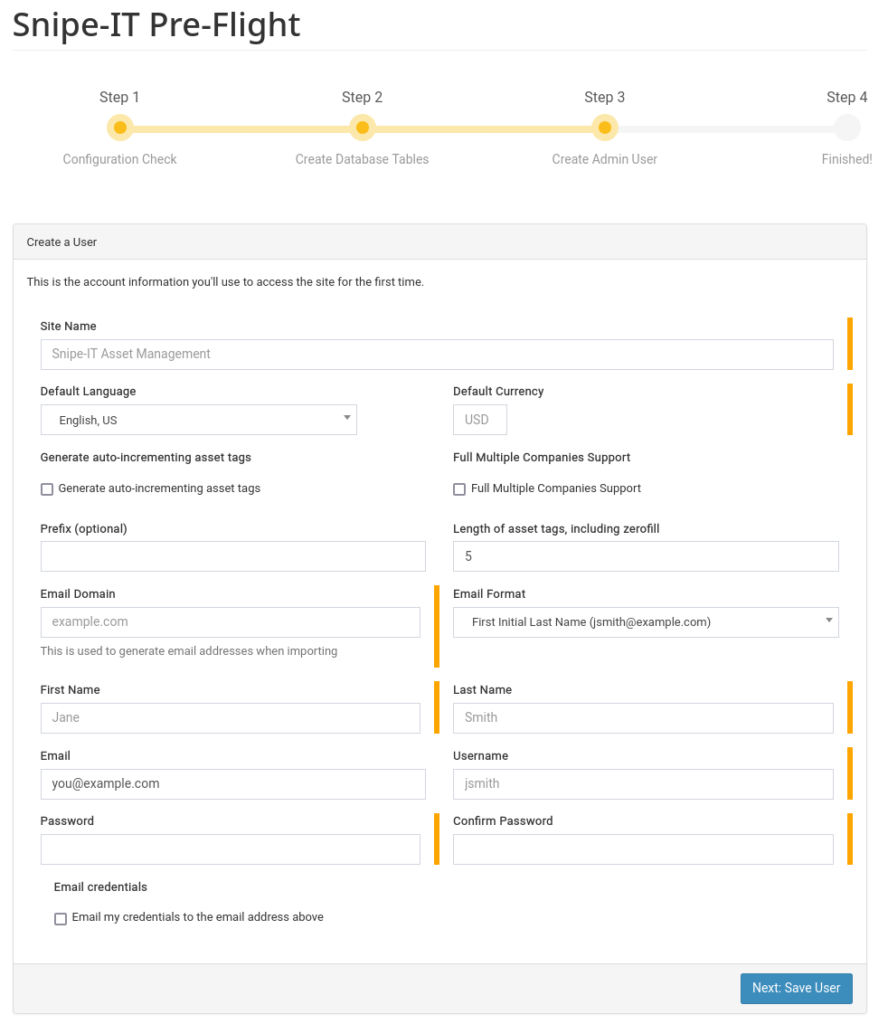
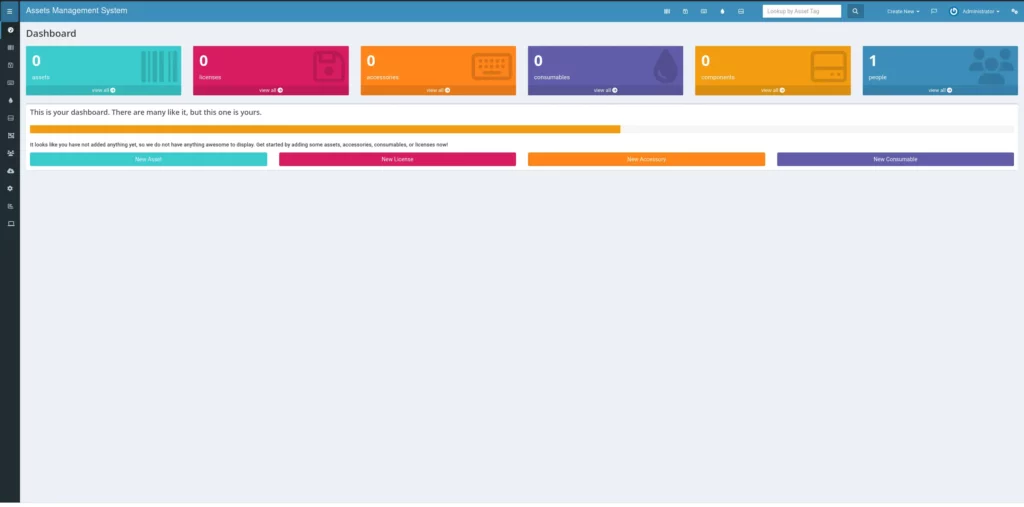
One last step, if you want to redirect http to https, add the following to the snipeit.conf file port 80 section.
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}Restart Apache, and that would be it. Enjoy!
apachectl -t
systemctl restart apache2






I get the error: “You don’t have permission to access this resource.”?
If you encounter this error during the initial browse to the Snipe-it page, make sure you have applied the proper permissions by making the Apache user the owner of the HTML directory.
I get the same. Giving apache ownership of the HTML directory doesn’t resolve it.